WebUSB hack: Bypassing browser Restrictions with U2F
Table of Contents
- 1. WebUSB hack: Bypassing browser Restrictions with U2F
- 2. U2F as a Backdoor to WebUSB
- 3. How the Exploit works
- 4. Security Implications and Limitations
- 5. Cool webusb Projects
- 6. Conclusion
- 7. how does the U2F workaround potentially impact the future of webusb development and browser security measures?
- 8. Unlocking WebUSB: A U2F Workaround Interview with Cybersecurity Expert, Dr.Anya sharma
- 9. WebUSB Security: A Balancing Act
- 10. U2F: An Unlikely WebUSB Enabler?
- 11. Diving Deeper: The Technical Mechanics
- 12. Security Implications: Risky Business?
- 13. The Future of WebUSB “hacks”
- 14. Practical WebUSB Applications
The WebUSB API, designed to expose USB devices to the web, faces security concerns and limited browser support. Though, a clever workaround leverages the global 2nd Factor (U2F) standard to unlock WebUSB-like functionality, even in browsers that don’t natively support it.
U2F as a Backdoor to WebUSB
The U2F standard is intended to bolster security through USB dongles for two-factor authentication. Ironically, its architecture allows for a bypass of WebUSB limitations. ArcaneNibble demonstrated this by using U2F-compatible firmware on a Raspberry Pi RP2040. By “hijacking the U2F payload,” the API can mimic WebUSB functions.
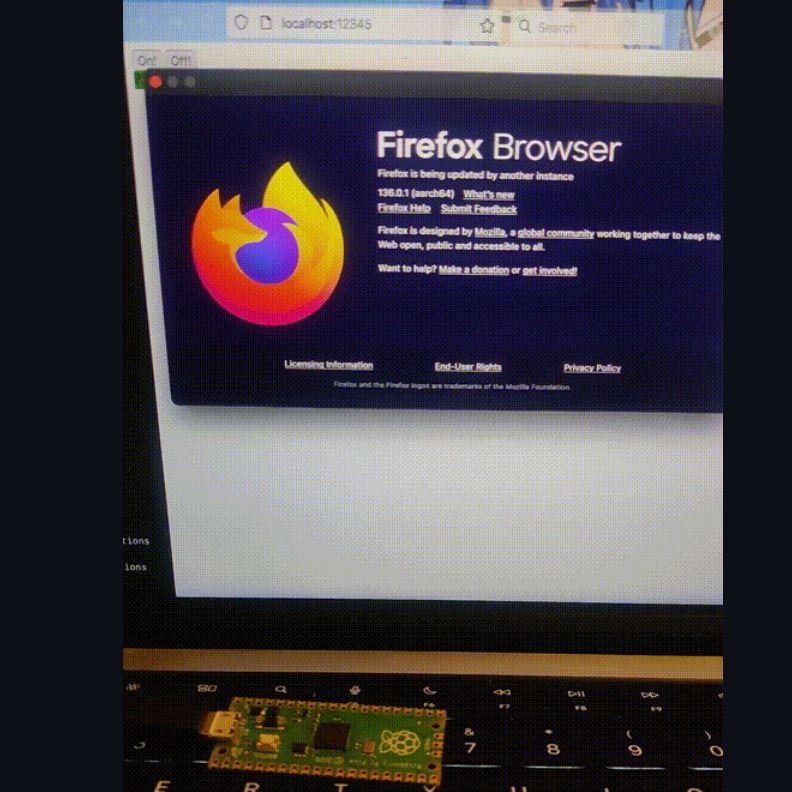
How the Exploit works
The key lies in the “opaque nature of the U2F key handle.” This allows arbitrary data to be embedded within it, facilitating data transfer from the U2F dongle to the host. Sending data back is more complex,involving manipulation of the ECDSA signature within the ASN.1 structure. This method succeeds as Firefox lacks signature validation, and Chrome performs only a basic range check.
Further simplifying the process, the MCU automatically confirms user presence by initiating the key handle with 0xfeedface. This eliminates the need for user interaction, though a fleeting popup may appear.
Security Implications and Limitations
- Isolated Risk: The exploit requires a specifically crafted USB device, leaving standard USB devices unaffected.
- Browser Compatibility: As of March 2025, this workaround is most effective in browsers with lenient U2F validation.
Cool webusb Projects
Despite the security considerations, WebUSB opens doors to exciting projects. Examples include:
- Interacting with custom hardware directly from a web browser.
- Creating web-based interfaces for controlling devices like Arduino boards.
As referenced previously, we’ve seen WebUSB used to create interactive badges and also a few projects that use it to allow web-based interfaces for controlling devices like Arduino boards.
Conclusion
While the WebUSB standard remains contentious, this U2F-based workaround demonstrates the ingenuity of developers in circumventing limitations. However, users should be aware of the potential security implications. Are you intrigued by the possibilities of WebUSB and ready to explore its potential? Share your thoughts and project ideas in the comments below!
how does the U2F workaround potentially impact the future of webusb development and browser security measures?
Unlocking WebUSB: A U2F Workaround Interview with Cybersecurity Expert, Dr.Anya sharma
Here at Archyde, we’re always keen to explore innovative solutions, especially in the ever-evolving landscape of web security. Today, we’re joined by Dr. Anya Sharma, a leading cybersecurity expert specializing in browser security and WebUSB vulnerabilities, to discuss a fascinating workaround using the U2F standard. Welcome, Dr. Sharma!
Thank you for having me. I’m excited to delve into this intriguing topic.
WebUSB Security: A Balancing Act
Dr. Sharma, for our readers who may be unfamiliar, could you briefly explain what WebUSB is and why its adoption has been somewhat limited?
Certainly. WebUSB is an API designed to allow websites to directly communicate with USB devices. The idea is fantastic – imagine controlling your Arduino directly from a webpage! Though, it raises critically important security concerns. Direct USB access from the web could be exploited for malicious purposes, leading to limited browser support to mitigate potential exploits.
U2F: An Unlikely WebUSB Enabler?
That makes sense. Now, this recent revelation of using the U2F standard as a workaround for WebUSB limitations is quite intriguing. How does this “hack,” as some might call it, actually work?
It leverages a loophole, really. The U2F standard uses USB dongles for two-factor authentication.The “key handle” within the U2F protocol is essentially an opaque data blob. Clever developers,like ArcaneNibble,have found a way to smuggle arbitrary data within this blob,effectively using the U2F authentication process as a data conduit. A Raspberry Pi RP2040 or similar device can be programmed to behave like a U2F dongle while together transmitting the desired webusb-like data.
Diving Deeper: The Technical Mechanics
So, data can be sent from the “dongle” to the browser. But what about sending data back the other way?
That’s where it gets trickier. Data going back relies on manipulating the ECDSA signature within the ASN.1 structure of the U2F response. this takes advantage of the fact that some browsers, notably Firefox and even Chrome to some extent, don’t perform rigorous validation of the signature. It’s essentially exploiting lenient browser security checks.
Security Implications: Risky Business?
Naturally, this raises some red flags. What are the security implications of using the U2F standard in this way?
While the risk is somewhat isolated – it requires a specifically crafted USB device – it’s crucial to understand that this isn’t a “free pass” to WebUSB. The security implications are real. This method circumvents intended browser security measures, and relying on lax signature validation is not a lasting or secure practice. It’s playing a game of cat and mouse between security researchers and browser developers.
The Future of WebUSB “hacks”
Given the potential risks and the likelihood of browser vendors patching these loopholes, what’s your outlook on the longevity of this U2F workaround?
I think its lifespan is limited. Browser vendors will likely tighten U2F validation and close these gaps.Eventually, this method will become unreliable. However, it serves as a valuable demonstration of the underlying demand for WebUSB-like functionality and pushes browser developers to find secure ways to implement that functionality, whether that’s through a revised WebUSB standard or a wholly different approach.
Practical WebUSB Applications
Despite the security concerns, are there any legitimate and exciting applications for WebUSB, or this workaround that could drive innovation even further?
Absolutely! The core idea of interacting with custom hardware directly from a web browser is incredibly appealing. Imagine web-based control panels for 3D printers, refined sensor monitoring systems controllable from a webpage, or even interactive educational tools that directly manipulate hardware. The possibilities are vast.
Thank you, Dr. Sharma, for shedding light on this fascinating workaround and the broader implications of webusb security. It’s certainly a topic that sparks a lot of debate and innovation!
My pleasure. Security is about constantly evolving and adapting, and innovative solutions are always welcome.
what do you think? are you intrigued by the possibilities of using WebUSB or worried about the security issues? Share your thoughts and project ideas in the comments below!


